Most software engineers use a version control system like Git to track changes in the project’s source code during software development. But when a software engineer uses Git, they usually include a git directory located at the root of the website to store all the version control information of the project, including the commit history of some files.
Following the best practices in cybersecurity, the .git directory should not be accessible to the public, but some software engineers are neglecting this practice and are simply uploading the entire project to the internet, and this is when information leaks occur.
Besides Git, there are many other version control systems out there such as CVS (Concurrent Version System), SVN (Apache Subversion), BZR (Bazaar), and HG (Mercurial).
Finding .git directory
There are many ways to find a .git directory, here are some of them:
- Google Search Engine
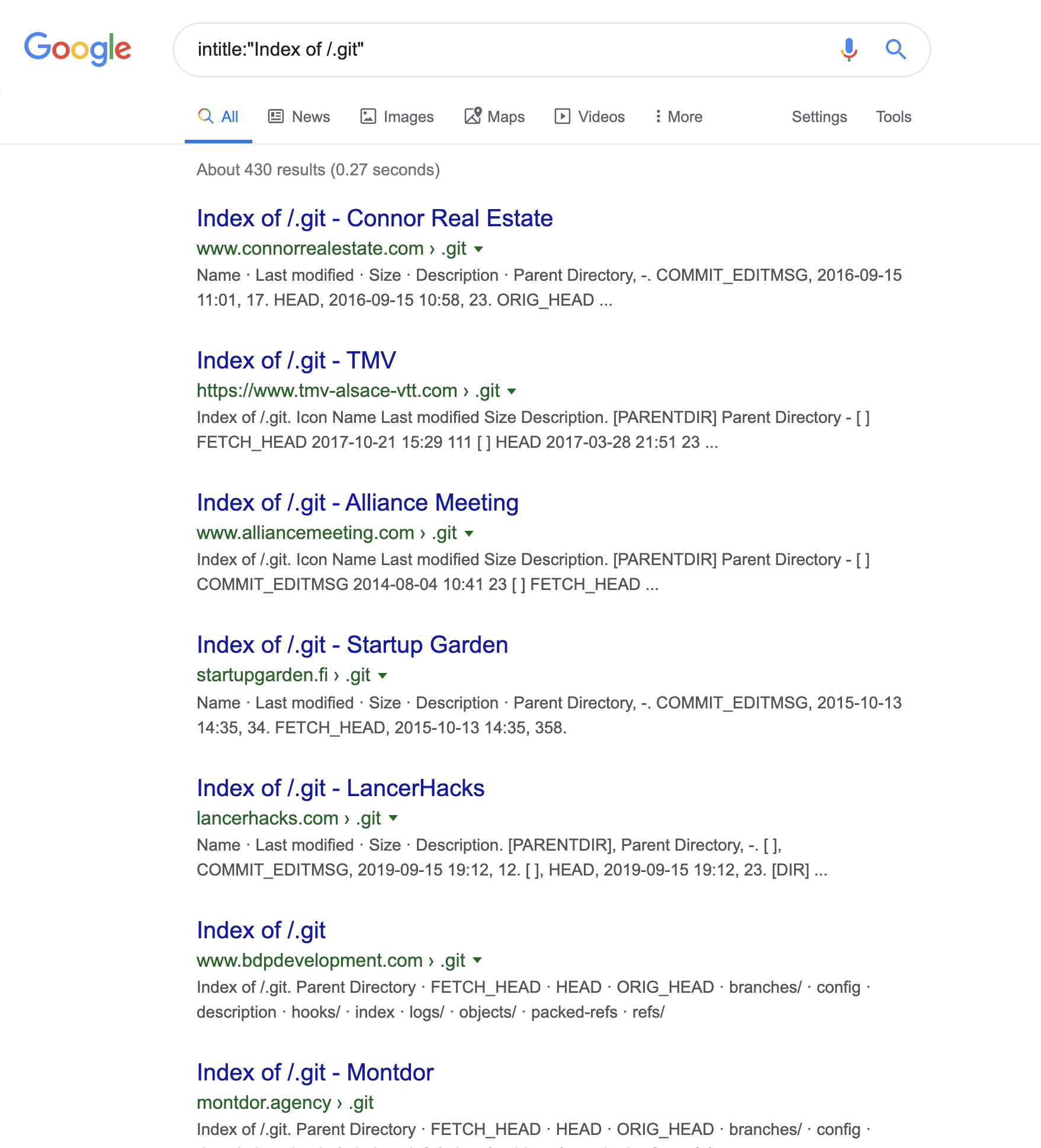
By simply searching for the following Google Dorkintitle:"Index of /.git", any user can find websites with a publicly exposed and accessible Git Repository.
- Shodan
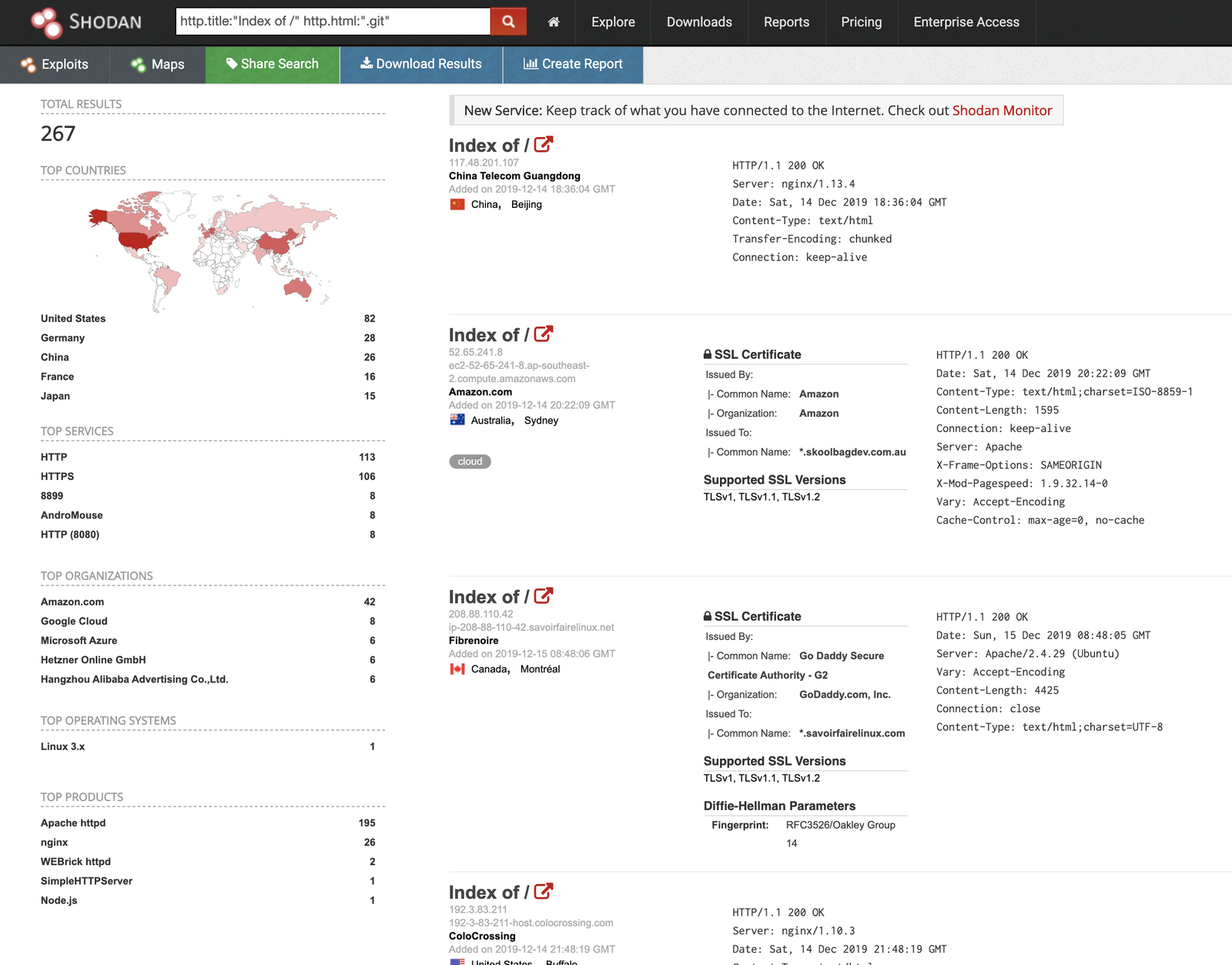
Shodan is the search engine for everything on the internet. Using the following queryhttp.title:"Index of /" http.html:".git", it will return you a list of websites with exposed .git repository.
- Open-Source Tools
There are many open-source tools that could help you find a .git directory.
GitTools – A tool created by @internetwache to Find, Dump, and Extract git.
Bruteforcing Tools like DirBuster, Dirsearch, Wfuzz, and dirb.
- DirBuster – https://tools.kali.org/web-applications/dirbuster
- Dirsearch – https://github.com/maurosoria/dirsearch
- Wfuzz – https://github.com/xmendez/wfuzz
- Dirb – https://tools.kali.org/web-applications/dirb
To check if the .git directory is publicly exposed, simply go to the root directory of the website then append /.git at the end of the URL.

Dumping the exposed .git repository
Using a tool called wget you can easily download or copy the whole directory recursively.

You may also use GitTool’s Dumper - https://github.com/internetwache/GitTools/tree/master/Dumper.
.git Structure
Executing the list command will give us the following:
- config - a file containing the configuration of the project.
- HEAD - a file containing a reference to the master branch.


Extracting the Files
Once you have the hash for the master branch, you can now execute the command git cat-file -p <master hash> to get the hash for the tree object which leads you to the files of the project by executing the same command.

To extract the source code of the website into a compressed file, execute the following command: git archive --format zip --output "source.zip" <master-hash>

And there you have it! You successfully downloaded the whole source code of the website.
Finding Juicy Information
Now that you have the source code, you can easily find hardcoded credentials, keys, or tokens using grep or by manually reading each file.
Protecting .git repository
There are many ways to protect your .git repository, and these are some of them:
- Deny users’ request to access .git through Nginx, Lighttpd, IIS, or Apache;
- Change the File Permission for .git directory; or
- Remove the directory before deploying the project/website online.
