It's now easy to host a third-party website page into your subdomain than before. On your DNS server, you will simply create a CNAME record and point it directly to a third party service. Too easy, right?
Well, taking over a subdomain with a misconfigured DNS record is too easy too.
Subdomain Takeover
Subdomain Takeover is an attack targeting subdomains of a domain with a misconfigured DNS record. That said, the hacker can fully take control of the vulnerable subdomain.
This kind of cyber attack is untraceable and affects popular service providers including GitHub, Squarespace, Shopify, Tumblr, Heroku and more.
Today I'll show you the process of finding identifying and claiming a vulnerable subdomain.
Subdomain Enumeration
Subdomain Enumeration is the process by which subdomains are identified and enumerated from a domain. Here are some of the various ways this can be done.
Open Source Tools
| Tool | Author | Details |
|---|---|---|
| Sudomy | Screetsec | Sudomy is a subdomain enumeration tool, created using a bash script, to analyze domains and collect subdomains in fast and comprehensive way. |
| Sublist3r | aboul3la | Sublist3r is a python tool designed to enumerate subdomains of websites using OSINT. |
| knock | guelfoweb | Knockpy is a python tool designed to enumerate subdomains on a target domain through a wordlist. |
| findomain | Edu4rdSHL | A cross-platform tool that use Certificates Transparency logs to find subdomains. |
| subfinder | projectdiscovery | subfinder is a subdomain discovery tool that discovers valid subdomains for websites by using passive online sources. |
Online Resources
| Tool | Description | Details |
|---|---|---|
| An Online Search Engine | Search subdomains using the following Google Dork: site:.domain.com | |
| Cloudflare | A useful tool to enhance site performance and security, accelerate the access speed and improve the visitors' experience. | Login to Cloudflare and just Add Target to get a list of subdomains from target's DNS server |
| Censys | A public search engine that enables researchers to quickly ask questions about the hosts and networks that compose the Internet. | Go to https://censys.io/domain and input your target domain to list down the subdomains. |
| Crt.sh | A web interface to a distributed database called the certificate transparency logs. | Go to https://crt.sh/ and input %.domain.com |
Subdomain Analysis and Exploitation
A well-known hacker named EdOverflow compiled a list of services that could be vulnerable to subdomain takeover, and he called it “Can I Take Over XYZ?”.
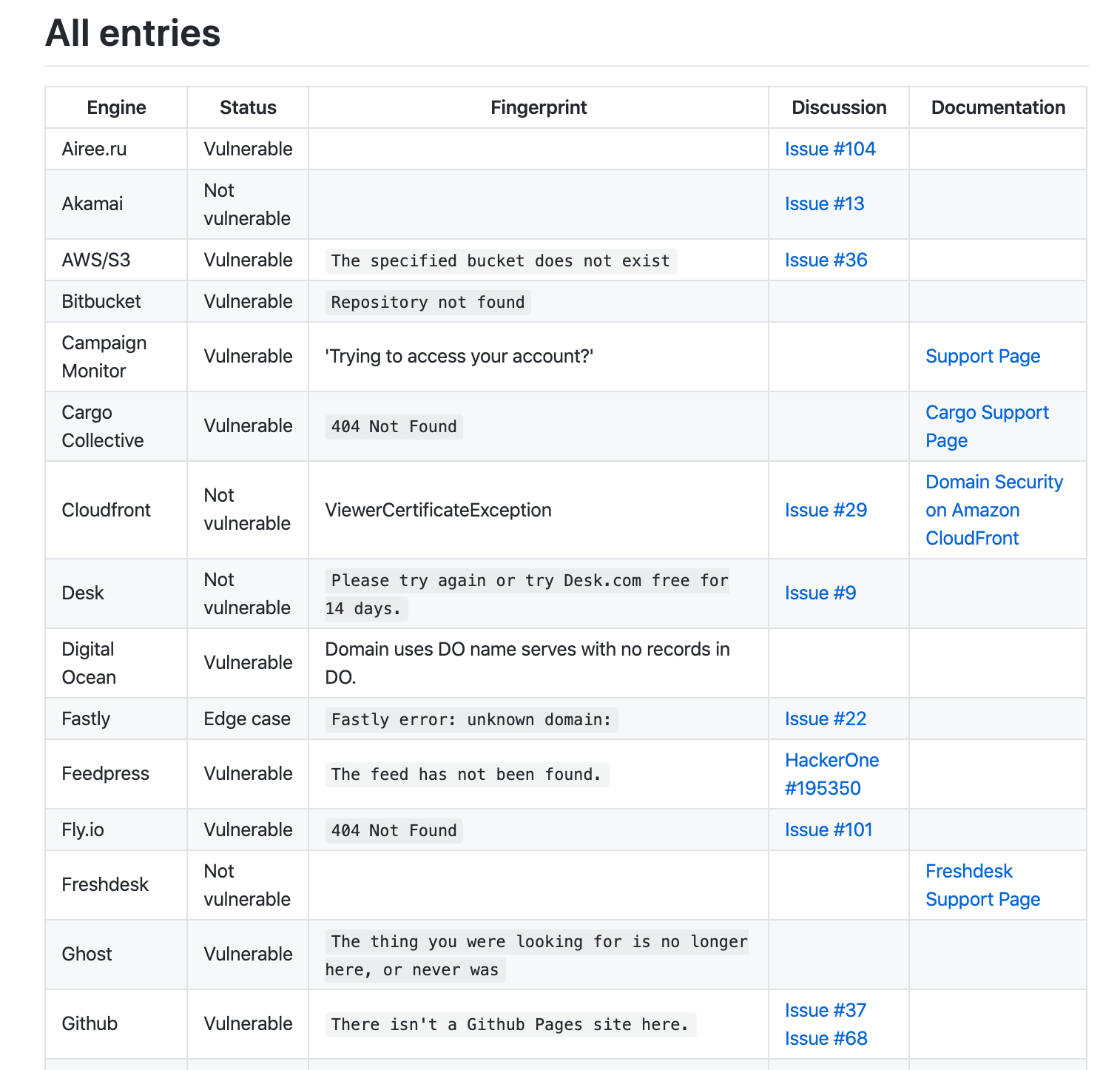
Below are some sample screenshots of vulnerable subdomains.
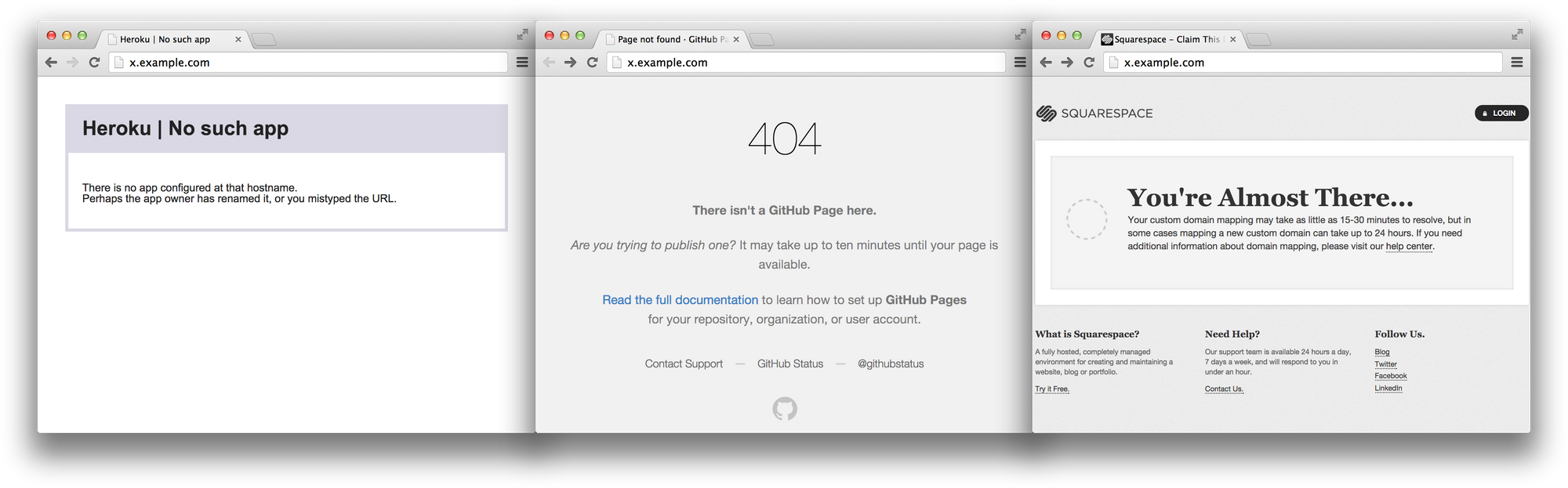
Once you come across one of those pages, you have a high chance to take over a vulnerable subdomain. Just follow the steps underneath:
- Create an account and resource to a third-party service where the vulnerable subdomain is pointed to.
- Claim and connect the vulnerable subdomain into your newly created third-party webpage.
- An attacker may now do as follows:
- Clone and imitate a real website;
- Add a malicious login form;
- Redirect the user to malicious resource;
- Steal sensitive information (e.g. API keys and Admin Credentials); or
- Completely destroy the company/organization credibility.
Real Life Findings
- Subdomain Takeover in USA.gov
The subdomainapi.usa.govwas pointed to a non-existing GitHub page and can be claimed by anyone. - Subdomain Takeover in Starbucks
The subdomains*.starbucks.comwas pointed to several third-party services like Azure and CloudApps with a non-existing resource which can be created to claim the pointed subdomains. - Subdomain Takeover in 9GAG
The subdomaincontact.9gag.comwas pointed to a third-party service Desk by Salesforce. It was pointed to a non-existing9gag.desk.comand anyone can create that page and connect it to the vulnerable subdomain. - Subdomain Takeover in Uber leading to Account Takeover
The subdomainsaostatic.uber.comwas pointed to Amazon CloudFront CDN. The reporter claimed it and exploited the auth process in auth.uber.com to allow himself to bypass the authentication and takeover accounts.
Protecting Subdomains from Takeovers
- Check the DNS records regularly for potential misconfiguration of the subdomains that point to third party services.
- Read the third-party service documentation to determine whether they have a secure domain-pointing process.
- Should you have been hacked, remove the DNS record pointing to the attacker's third-party service.
Secuna is the first and only community-powered cybersecurity testing platform in the Philippines helping startups and SMEs by connecting them to vetted security researchers to find and fix security vulnerabilities before they can be exploited by cybercriminals.
