When there’s an emergency, someone can just call 911 and they get connected to the right personnel to help them resolve the emergency. For the internet, when someone discovers a security bug in an app or a website, there’s no easy way to report it to the company. In most cases, this bug is an emergency that, unfortunately, is just left unresolved until a malicious hacker exploits it.
At Secuna, we built a platform -- Secuna Discover -- where security vulnerabilities can be reported to companies before people with malicious intent exploit them. And now, we are further expanding it to cover products, apps and websites that are not even registered in the Secuna Discover platform via our Coordinated Vulnerability Disclosure Assistance program.
https://app.secuna.io/coordinated-vulnerability-disclosure-assistance
Coordinated Vulnerability Disclosure Assistance
Coordinated Vulnerability Disclosure (CVD) is the process of gathering security vulnerability information from security researchers, coordinating the sharing of that information between relevant stakeholders, and disclosing the existence of security vulnerabilities and their mitigations to various stakeholders, including the public.
Secuna's Coordinated Vulnerability Disclosure Assistance (CVDA) program aims to promote the mantra: “If You See Something, Say Something.” This means, when a person -- usually a security researcher -- discovers a vulnerability, he/she reports it immediately to the affected organization to warn them about possible security risks.
Secuna follows the ISO/IEC 29147:2018 standard and Carnegie Mellon University's CERT Guide to Coordinated Vulnerability Disclosure to provide this program to assist security researchers in reporting security vulnerabilities to any organization.
How does it work?

Why does Secuna offer this program?
Security researchers are at risk of disclosing security vulnerabilities to organizations that do not have a Vulnerability Disclosure Policy. Would the security researcher be given a warm response or a legal threat? This kind of uncertainty intensifies the deterrent effect causing security vulnerabilities to go unreported, making the Internet less secure than it should be.
But what do you think currently happens when a security researcher discovers a security vulnerability? Read on to see how it is currently done, albeit inefficiently, and how we plan to make vulnerability reporting more effective and efficient.
When a security researcher finds a security vulnerability in an app or a website of an organizations, this is how it is usually reported:
- Reporting via Email
Since most organizations do not have a dedicated security email, the researcher sends a message to the customer support email or help desk, who in turn, don’t know how to handle the report. So support emails are usually blackholes for these types of reports. - Full Disclosure via Blog
Where there is still no response from the organization, some security researchers disclose their findings publicly, mainly to inform the public about the vulnerability and how to protect themselves from potential cyberattacks due to that vulnerability.
As an example, a Dutch security researcher, Willem De Groot, published a blog after discovering a malware embedded in the website of a local broadcasting company. - Mentioning concerned parties via Twitter
When a security researcher does not get a valid response to their email, they tweet it publicly and mention the Twitter page of the organization hoping to get a response.
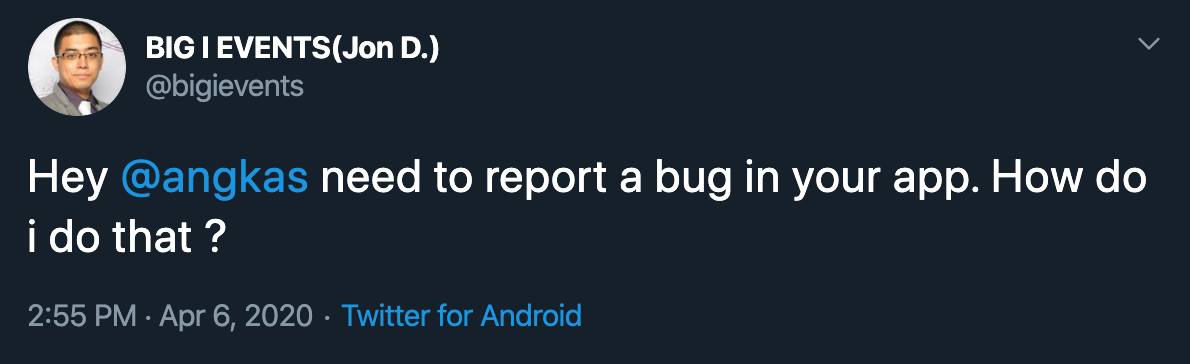
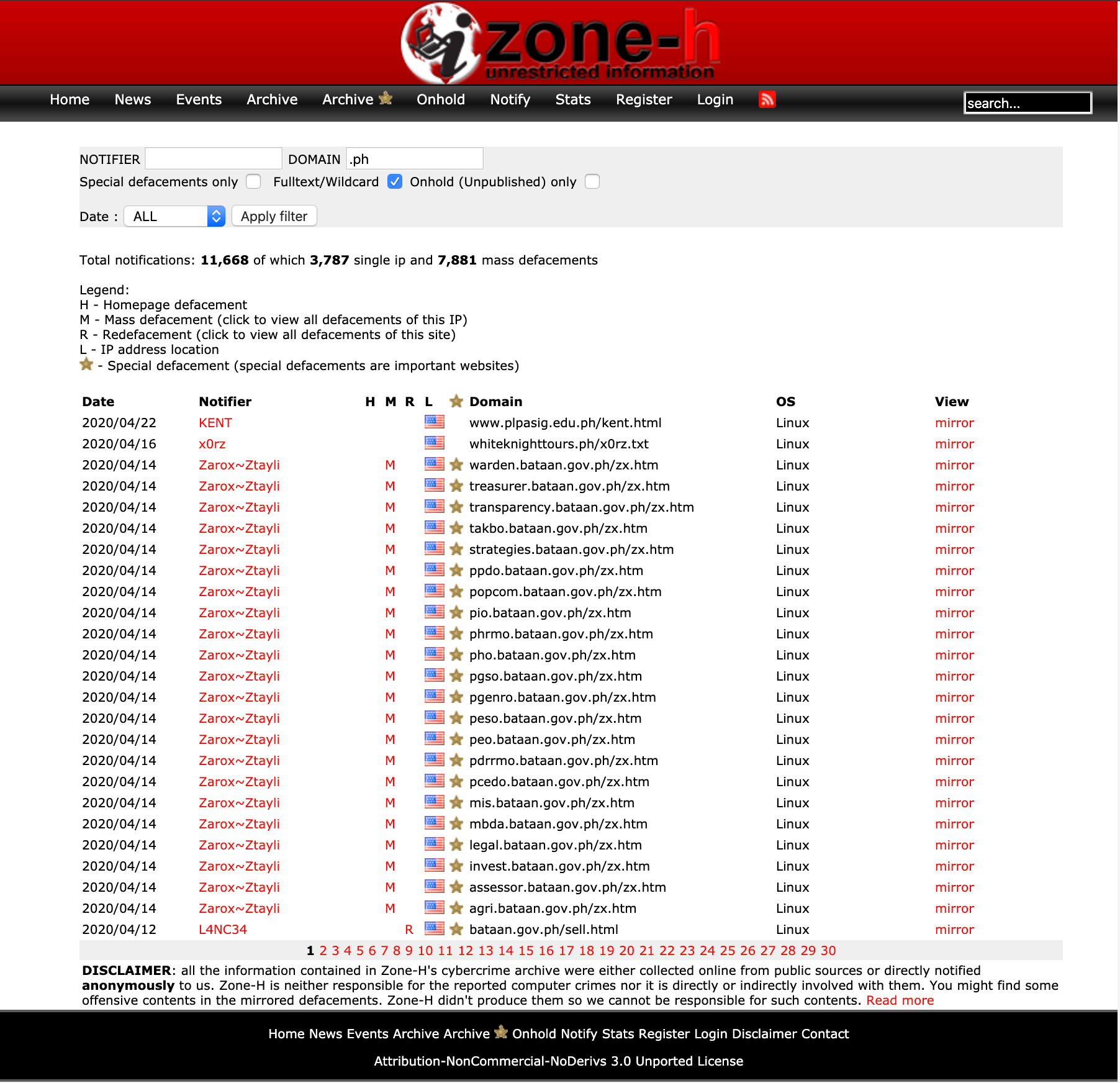
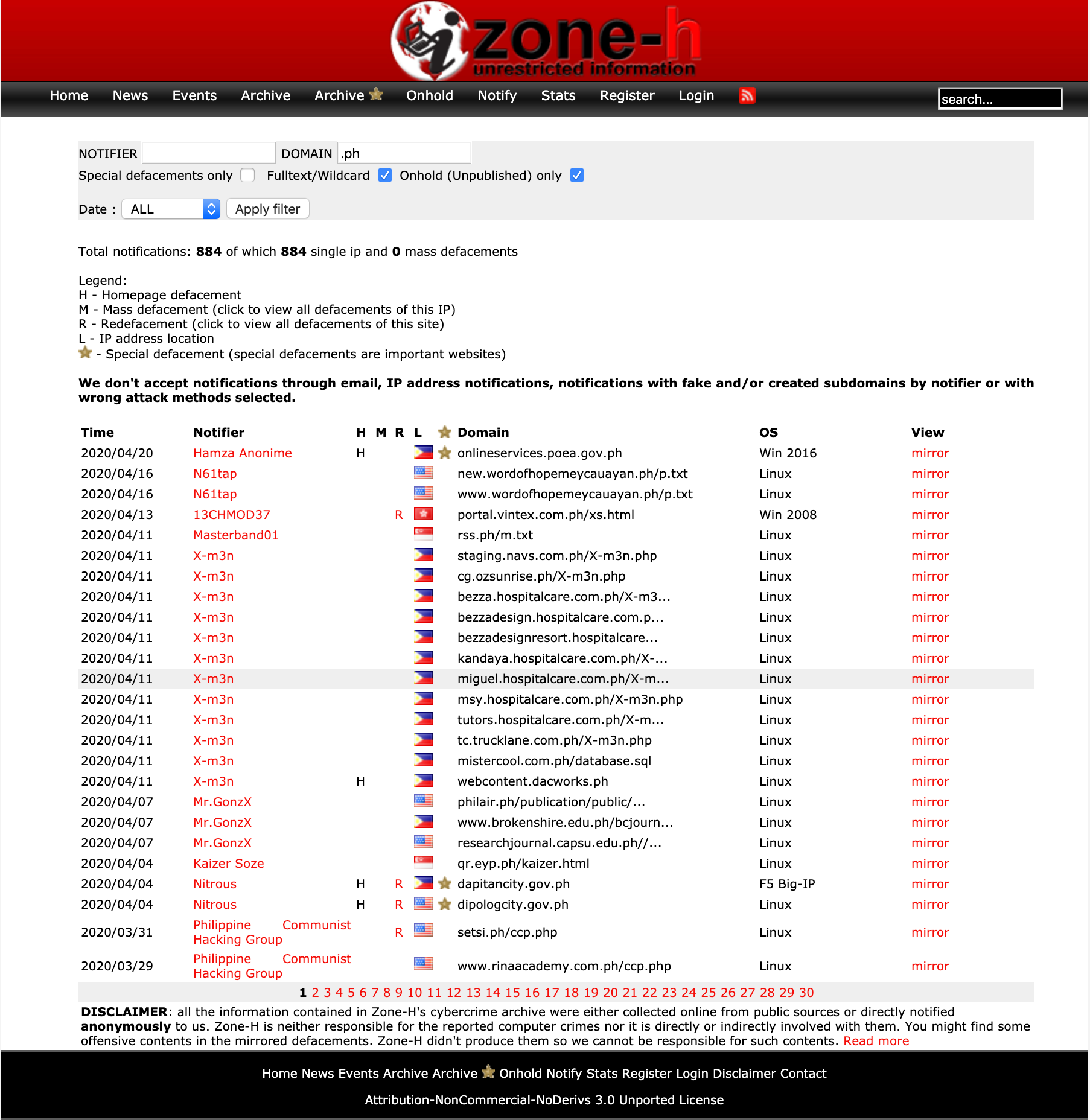
While security researchers (good hackers) try their best to inform organizations, there are some cybercriminals who find the same security vulnerability and exploit it for fun, money, fame, etc. Globally, cybercriminals use Zone-H website to list all the defaced and compromised websites. Screenshots below is a recorded list of breached/defaced/hacked websites in the Philippines. And we know for a fact that this list will be growing faster in the next few months.
Quick Reminders from Secuna:
- We do not condone, support, or encourage security researchers to find security vulnerabilities in any organization without their permission.
- We require security researchers to reach out the organization first before requesting an assistance to us.
- We cannot guarantee success in contacting the affected organization.
- We will try out best to reach out to the affected organization to notify and inform them about the potential security vulnerability.
- We will only provide the security vulnerability information to the appropriate point of contact of the organization once we verified their identity.
Should you have questions about Secuna's Coordinated Vulnerability Disclosure Assistance program, feel free to drop an email to [email protected].
